News is spreading across the web about the Heartbleed bug that affects OpenSSL. This may seem like Greek to you but if you are doing anything on the web, you MUST pay attention. First, don't panic. Second, read about what's happening below. And third, change your passwords.
UPDATE 4-10-14: As we all dig deeper into this OpenSSL flaw, it appears that researchers caught it first. If hackers found the flaw first, they are certainly being quiet about it as one would expect. Keep in mind if someone with bad intentions downloaded data through this flaw, they would still have to decode it. There is still no need for panic but you should take action. See below for an update on the responses and a list of impacted sites.
What is Heartbleed Bug?
Officially called CVE-2014-0160, it was named Heartbleed Bug by security firm
Codenomicon. They posted a
comprehensive run down on the bug for techies. The bug is a flaw in the Secure Socket Layer (SSL), an open source encryption standard that is used by a majority of websites. This makes about
2/3 of the web vulnerable to security breeches.
For non-techies, SSL is most visible when you see a lock on your web browser next to the URL. This
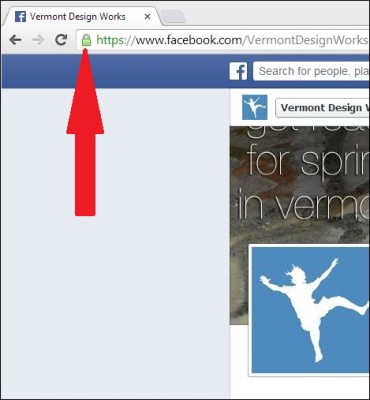
lets you know that there is data encryption for whatever information you send back and forth to the server powering that website. All sizes of businesses in almost every industry use OpenSSL. Examples are banking, credit card companies, online shopping sites, social media, email, and anywhere that you enter a password.
Once you log-in to a site, your computer is now talking to the server on the other end of that website. From time to time, the website's server will send a data packet that asks for a response to check that the secure connection is still active. This is called a heartbeat. Think of it like the server asking, "Hello, is this connection still alive?" and your computer responds with a heartbeat response. All of this data exchange is encrypted by OpenSSL as well.
The Heartbleed Bug mimics these "heartbeat" check-ins between servers and computers. It asks computers send data back. This data request can be
any data stored on a website's server from passwords and credit card numbers to anything that you uploaded to that website.
This means an attacker could quite feasibly get a server to spit out its secret keys, allowing them to read to any communication that they intercept like it wasn’t encrypted it all. Armed with those keys, an attacker could also impersonate an otherwise secure site/server in a way that would fool many of your browser’s built-in security checks. ~TechCrunch
Discovery of the bug is being attributed to Google security researcher Neel Mehta. It has been
demonstrated multiple times in the past 24 hours through well-intentioned hacks by researchers (by the way, these researchers hacked Yahoo multiple times so we advise that you change any Yahoo password quickly).
"According to the researchers who discovered the flaw, the code has been in OpenSSL for about two years, and using it doesn't leave a trace." ~Business Insider
What to do? Don't Panic
To quote the immortal words of Dougls Adams, "Don't Panic." But PAY ATTENTION! This bug has been around for awhile; however it is serious. To give you an idea of how serious, network engineers are using these descriptors for Heartbleed: massive, very serious, and devastating. Remember, these are usually unflappable engineers who deal with server attacks all day every day. You will never see them running around an office as if their hair is on fire; yet this bug has everyone moving at an extraordinarily quick pace to install patches.
Here at VDW, our network engineers installed patches on our OpenSSL certificates and put safeguards in place on all of our servers today.
If you are a VDW client who manages your own OpenSSL certificates: please check with your OpenSSL provider to ensure this is fixed.
And Now....Change Your Passwords

Now that you know your business websites are being fixed, it is time to pay attention to your personal accounts. When an internet-wide vulnerability like this comes to light, it is best to change your passwords.
ALL passwords. Starting with your online banking passwords. There's no telling where a password was picked up by the bug.
“"Change your password, since this could easily have been fished out of your communications at any point in the last two years." ~NPR
The bigger the company and their website, the longer it is going to take for them to patch the bug. Therefore, give them some time to fix the bug and then change your password.
Update April 10, 2014:
All reports agree that Heartbleed is a serious flaw. The "don't panic" mantra is still in effect with the caveat that you take action. First, check with the sites to ensure they have patched the flaw. Second, change your passwords. ALL of them.
Updates for Techies: Google's
blog on online security gives a brief run down on what they found and what they did about it. Carnegie Mellon released a
far more detailed bulletin.
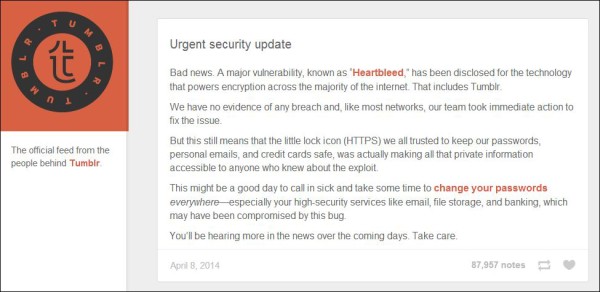
As you log-into accounts today, you might see reminders to change your passwords. So far, Tumblr is the most forthright about the flaw and what they did about it. Once you log-in, the top of the page suggests that you change your password and provides a
quick link to an explanation (see photo below).
Lists of vulnerable sites are being updated hourly. GitHub released the
first mid-day on April 9th. Mashable pounded on the doors of every company for statements like old school reporters. They compiled a
detailed list of top sites, if they were vulnerable to the flaw, and if they patched it. Standouts on the list (remember, don't panic) are: Gmail, Yahoo, GoDaddy, Inuit/TurboTax, and LastPass.
If one of your favorite sites appears on any "unclear" or "vulnerable" list, we recommend that you change your passwords. If a site is on the safe list and you haven't changed your password in awhile, this might be a good time to do so anyway because so many other sites were impacted. Finally, if you have questions about a particular service or account, we recommend that you ask direct questions to that company. While everyone in the tech industry is putting safeguards in place, they are answering customers' questions as quickly as they can.
 lets you know that there is data encryption for whatever information you send back and forth to the server powering that website. All sizes of businesses in almost every industry use OpenSSL. Examples are banking, credit card companies, online shopping sites, social media, email, and anywhere that you enter a password.
Once you log-in to a site, your computer is now talking to the server on the other end of that website. From time to time, the website's server will send a data packet that asks for a response to check that the secure connection is still active. This is called a heartbeat. Think of it like the server asking, "Hello, is this connection still alive?" and your computer responds with a heartbeat response. All of this data exchange is encrypted by OpenSSL as well.
The Heartbleed Bug mimics these "heartbeat" check-ins between servers and computers. It asks computers send data back. This data request can be any data stored on a website's server from passwords and credit card numbers to anything that you uploaded to that website.
lets you know that there is data encryption for whatever information you send back and forth to the server powering that website. All sizes of businesses in almost every industry use OpenSSL. Examples are banking, credit card companies, online shopping sites, social media, email, and anywhere that you enter a password.
Once you log-in to a site, your computer is now talking to the server on the other end of that website. From time to time, the website's server will send a data packet that asks for a response to check that the secure connection is still active. This is called a heartbeat. Think of it like the server asking, "Hello, is this connection still alive?" and your computer responds with a heartbeat response. All of this data exchange is encrypted by OpenSSL as well.
The Heartbleed Bug mimics these "heartbeat" check-ins between servers and computers. It asks computers send data back. This data request can be any data stored on a website's server from passwords and credit card numbers to anything that you uploaded to that website.
 Now that you know your business websites are being fixed, it is time to pay attention to your personal accounts. When an internet-wide vulnerability like this comes to light, it is best to change your passwords. ALL passwords. Starting with your online banking passwords. There's no telling where a password was picked up by the bug.
Now that you know your business websites are being fixed, it is time to pay attention to your personal accounts. When an internet-wide vulnerability like this comes to light, it is best to change your passwords. ALL passwords. Starting with your online banking passwords. There's no telling where a password was picked up by the bug.
 Lists of vulnerable sites are being updated hourly. GitHub released the first mid-day on April 9th. Mashable pounded on the doors of every company for statements like old school reporters. They compiled a detailed list of top sites, if they were vulnerable to the flaw, and if they patched it. Standouts on the list (remember, don't panic) are: Gmail, Yahoo, GoDaddy, Inuit/TurboTax, and LastPass.
If one of your favorite sites appears on any "unclear" or "vulnerable" list, we recommend that you change your passwords. If a site is on the safe list and you haven't changed your password in awhile, this might be a good time to do so anyway because so many other sites were impacted. Finally, if you have questions about a particular service or account, we recommend that you ask direct questions to that company. While everyone in the tech industry is putting safeguards in place, they are answering customers' questions as quickly as they can.
Lists of vulnerable sites are being updated hourly. GitHub released the first mid-day on April 9th. Mashable pounded on the doors of every company for statements like old school reporters. They compiled a detailed list of top sites, if they were vulnerable to the flaw, and if they patched it. Standouts on the list (remember, don't panic) are: Gmail, Yahoo, GoDaddy, Inuit/TurboTax, and LastPass.
If one of your favorite sites appears on any "unclear" or "vulnerable" list, we recommend that you change your passwords. If a site is on the safe list and you haven't changed your password in awhile, this might be a good time to do so anyway because so many other sites were impacted. Finally, if you have questions about a particular service or account, we recommend that you ask direct questions to that company. While everyone in the tech industry is putting safeguards in place, they are answering customers' questions as quickly as they can.
